The enhanced connectivity that less expensive, smaller, and faster chips have enabled via the Industrial Internet of Things (IIoT) and Industry 4.0 has both increased the amount of valuable data that business leaders are able to access to improve their manufacturing operations as well as the vulnerability of production facilities to bad actors. As a result of the growing amount of data being transferred to and from industrial facilities, there has been a steady increase in the number of cyberattacks seen across industrial automation that has led to significant adverse business impacts. This has made cybersecurity a critical business risk that can either be addressed proactively…or as a reactive measure to try to get manufacturing back online, to manage the press and customer reaction of a down facility, and to attempt to create an effective security strategy.
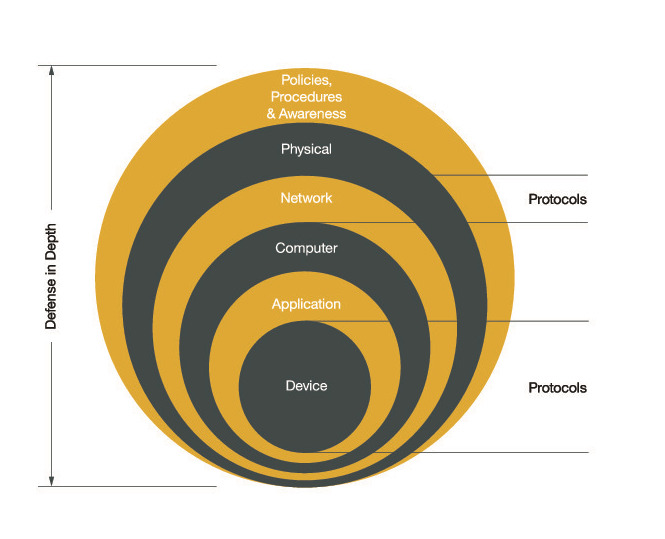
One of the most important ways to reduce the attack profile of a business is to implement a defense-in-depth architecture. A bad actor can be a singular, highly skilled person, a cooperative group, or even a nation state. With that in mind, it’s necessary to create a defense that includes many layers of deterrence. ODVA’s cybersecurity approach follows a defense-in-depth architecture by providing guidance and technologies to strengthen user’s systems from top to bottom.
Physical Security
Physical security is a valuable consideration given that wireless networks can be potentially reached outside of company property, open USB ports invite spyware, and lost electronic entrance security keys allow uninvited access that can significantly increase the attack vector of a facility. Contractors and supply chain partners cannot be forgotten about either as they can have access into critical operational technology systems or can be the weak link in the supply chain if they are an easy target due to limited security measures. ODVA’s guide “Securing EtherNet/IP Networks” provides best practices for ensuring the physical security of your network.
Keep in mind though that no matter how tough a single cybersecurity technology is to defeat, it can eventually be overcome with enough time and resources. That’s why a holistic defense-in-depth security strategy is so important to adopt. Staff training, physical lockouts, network switch firewalls and deep packet inspection, updated computer virus protection, patched applications, and device defense such as ODVA’s CIP Security™ network extension for EtherNet/IP™ can all play a role in keeping intruders out.

CIP Security
CIP Security, a cybersecurity network extension for EtherNet/IP, includes robust, proven, and open security technologies including TLS (Transport Layer Security) and DTLS (Datagram Transport Layer Security); cryptographic protocols used to provide secure transport of EtherNet/IP traffic, hashes or HMAC (keyed-Hash Message Authentication Code) as a cryptographic method of providing data integrity and message authentication to EtherNet/IP traffic; and encryption as a means of encoding messages or information in such a way as to prevent reading or viewing of EtherNet/IP data by unauthorized parties.
CIP Security also uses several open, common, ubiquitous technologies for user authentication, including OAuth 2.0 and OpenID Connect for cryptographically protected token-based user authentication, JSON Web Tokens (JWT) as proof of authentication, usernames and passwords, and X.509 certificates to provide cryptographically secure identities to users and devices. Additionally, CIP Security can provide information assurances for resource-constrained devices by requiring fewer mandatory features. Adding device level security provides a last level of defense for your most critical devices such as those used for motion control.
CIP Security is designed to be able to be used for those devices where the risk to life, property, and operations is the most critical. This means that CIP Security can be deployed in only those zones where workers could potentially be hurt by motion equipment, in devices that could reveal product recipes or manufacturing process secrets, or in lines that could cause great environmental damage. Further, CIP Security is designed so that different profiles can be applied where needed. For example, the User Authentication Profile may not be applied in a device which doesn’t have strong needs for user authentication yet does have high performance optimization needs. Learn more about CIP Security here.
![]()
Industrial Ethernet Security Harmonization Group (IESHG)
The Industrial Ethernet Security Harmonization Group (IESHG) is one of many collaborative activities in which ODVA is engaged to ensure that end users across industries benefit from a consistent application of the technologies they utilize. As a part of the IESHG, ODVA joins other industrial automation standards development organizations FieldComm Group, OPC Foundation, and PI to work to harmonize cybersecurity strategies and concepts, so that end users do not face unnecessary complexity when using security concepts in their automation systems.
ODVA is pleased to collaborate with leading standards development organizations in the IESHG to create greater commonality among key security terms and concepts within the automation industry. Providing end users with common education resources along with unique defense in depth network options, such as CIP Security, will enable greater solution adoption and ultimately more secure facilities.
The IESHG has released a FAQ whitepaper in order to explain different topics of the security concepts of industrial automation environments, such as Public-key infrastructures, variations of certificate types, and certificate management tools. Also, a presentation from ODVA’s Industry Conference is available here, which provides an in-depth look at the collaborative benefits of the IESHG.
The IESHG is exploring additional concepts and anticipates releasing more whitepapers in the future.


